Active Directory (AD) is a utility designed for the Microsoft Server operating system. It was originally created as a lightweight algorithm for accessing user directories. Since the version of Windows Server 2008, integration with authorization services has appeared.
Gives you the ability to comply with a group policy that applies the same type of settings and software on all controlled PCs using System Center Configuration Manager.
If in simple words for beginners, this is a server role that allows you to manage all accesses and permissions on the local network from one place
Functions and purposes
Microsoft Active Directory - (the so-called directory) a package of tools that allows you to manipulate users and network data. primary goal Creation - Facilitate the work of system administrators in extensive networks.
Directories contain various information related to users, groups, network devices, file resources - in a word, objects. For example, user attributes that are stored in the directory should be the following: address, login, password, mobile phone number, etc. The directory is used as authentication points, with which you can find the necessary information about the user.
Basic concepts encountered in the course of work
There are a number of specialized concepts that apply when working with AD:
- The server is the computer that contains all the data.
- The controller is a server with the AD role that handles requests from people using the domain.
- An AD domain is a collection of devices united under one unique name that simultaneously use a common directory database.
- The data store is the part of the directory that is responsible for storing and retrieving data from any domain controller.
How active directories work
The main principles of work are:
- Authorization, with which it becomes possible to use a PC on the network simply by entering a personal password. In this case, all information from the account is transferred.
- security. Active Directory contains user recognition features. For any network object, you can remotely, from one device, set the necessary rights, which will depend on the categories and specific users.
- Network administration from one point. While working with Active Directory, the system administrator does not need to re-configure all PCs if you need to change access rights, for example, to a printer. Changes are made remotely and globally.
- Complete DNS integration. With its help, there is no confusion in AD, all devices are designated in the same way as in the World Wide Web.
- large scale. A collection of servers can be controlled by a single Active Directory.
- Search is made according to various parameters, for example, computer name, login.
Objects and Attributes
Object - a set of attributes, united under its own name, representing a network resource.
Attribute - characteristics of the object in the catalog. For example, these include the user's full name, his login. But the attributes of a PC account can be the name of this computer and its description.
“Employee” is an object that has the attributes “Name”, “Position” and “TabN”.
LDAP container and name
Container is a type of object that can consist of other objects. A domain, for example, may include account objects.
Their main purpose is object ordering by type of signs. Most often, containers are used to group objects with the same attributes.
Almost all containers map to a collection of objects, and resources map to a unique Active Directory object. One of the main types of AD containers is the organization unit, or OU (organizational unit). Objects that are placed in this container belong only to the domain in which they are created.
Lightweight Directory Access Protocol (LDAP) is the basic algorithm for TCP/IP connections. It was created to reduce the amount of nuance during access to directory services. Also, LDAP defines the actions used to query and edit directory data.
Tree and site
A domain tree is a structure, a collection of domains that share a common schema and configuration, form a common namespace and are linked by trust relationships.
A forest of domains is a collection of trees linked together.
Site - a collection of devices in IP subnets, representing the physical model of the network, the planning of which is performed regardless of the logical representation of its construction. Active Directory has the ability to create n sites or combine n domains under one site.
Installing and configuring Active Directory
Now let's go directly to setting up Active Directory using Windows Server 2008 as an example (on other versions, the procedure is identical):

Click on the “OK” button. Note that these values are not required. You can use the IP address and DNS from your network. 
- Next, you need to go to the "Start" menu, select "Administrative Tools" and "".

- Go to the “Roles” item, select the “ Add Roles”.

- Select "Active Directory Domain Services", click "Next" twice, and then "Install".

- Wait for the installation to finish.

- Open Start Menu -“ Run". Enter dcpromo.exe in the field.

- Click "Next".

- Select item “ Create a new domain in a new forest” and click “Next” again.

- In the next window, enter a name, click "Next".

- Choose Compatibility Mode(Windows Server 2008).

- In the next window, leave everything as default.

- will start configuration windowDNS. Since it was not used on the server before, the delegation was not created.

- Select a directory for installation.

- After this step, you need to set administration password.
To be secure, the password must meet the following requirements:

After AD completes the component configuration process, you must restart the server.


The configuration is complete, the snap-in and the role are installed in the system. You can install AD only on Windows of the Server family, regular versions, such as 7 or 10, can only allow you to install the management console.
Administration in Active Directory
By default, in Windows Server, the Active Directory Users and Computers console works with the domain to which the computer belongs. You can access computer and user objects in this domain through the console tree or connect to another controller.
The same console tools allow you to view Extra options objects and search for them, you can create new users, groups and change from permissions.
By the way, there is 2 types of groups in Active Directory - security and distribution. Security groups are responsible for delimiting access rights to objects, they can be used as distribution groups.
Distribution groups cannot differentiate rights, but are used primarily to distribute messages on the network.
What is AD Delegation
Delegation itself is transfer of part of the permissions and control from the parent object to the other responsible party.
It is known that each organization has several system administrators in its headquarters. Different tasks should be assigned to different shoulders. In order to apply changes, you must have rights and permissions, which are divided into standard and special. Special - apply to a specific object, while standard - a set of existing permissions that make certain functions available or unavailable.
Establishing Trust Relationships
There are two kinds of trust relationships in AD: "unidirectional" and "bidirectional". In the first case, one domain trusts another, but not vice versa, respectively, the first has access to the resources of the second, and the second does not have access. In the second form, trust is “mutual”. There are also "outgoing" and "incoming" relationships. In outbound, the first domain trusts the second, thus allowing users of the second to use the resources of the first.
During installation, the following procedures should be carried out:
- Check network connections between controllers.
- Check settings.
- Tune name resolution for external domains.
- Create connection from the trusting domain.
- Create a connection from the side of the controller to which the trust is addressed.
- Check the created one-way relationships.
- If a there is a need in the establishment of bilateral relations - to make the installation.
Global Directory
This is the domain controller that keeps copies of all objects in the forest. It gives users and programs the ability to search for objects in any domain in the current forest using attribute discoverers included in the global catalog.
The Global Catalog (GC) includes a limited set of attributes for every forest object in every domain. It receives data from all domain directory partitions in the forest and replicates it using the standard Active Directory replication process.
The schema determines whether the attribute will be copied. There is a possibility configuring additional features, which will be re-created in the global catalog using the “Active Directory Schema”. To add an attribute to the global catalog, you need to select the replication attribute and use the “Copy” option. This will create a replication of the attribute to the global catalog. Attribute parameter value isMemberOfPartialAttributeSet will become true.
In order to find out the location global directory, you need to enter on the command line:
Dsquery server –isgc
Data replication in Active Directory
Replication is a copying procedure that is carried out when it is necessary to store equally up-to-date information that exists on any controller.
It is produced without operator intervention. There are the following types of replica content:
- Data replicas are created from all existing domains.
- Data schema replicas. Because the data schema is the same for all objects in the Active Directory forest, its replicas are preserved across all domains.
- configuration data. Shows building copies among controllers. The information applies to all domains in the forest.
The main types of replicas are intra-node and inter-node.
In the first case, after the changes, the system waits, then notifies the partner to create a replica to complete the changes. Even in the absence of changes, the replication process occurs after a certain period of time automatically. After applying breaking changes to directories, replication occurs immediately.
Replication procedure between nodes happens in between minimal load on the network, this avoids information loss.
Setting up Active Directory is a fairly simple process and is covered in many resources on the Internet, including official ones. However, on my blog, I can't help touching on this point, since most of the following articles will be based in one way or another on the environment, which I plan to set up right now.
If you are interested in the Windows Server topic, I recommend that you refer to the tag on my blog. I also recommend that you read the main article on Active Directory -
I plan to deploy the AD role on two virtual servers (future domain controllers) in turn.
- The first step is to set the appropriate server names, for me it will be DC01 and DC02;
- Next, write static network settings(I will discuss this point in detail below);
- Install all system updates, especially security updates (for CD this is important as for any other role).

At this stage, you need to decide what domain name will you have. This is extremely important, because then changing the domain name will be a very big problem for you, although the renaming script is officially supported and implemented for a long time.
Note: n Some reasoning, as well as many links to useful material, you can find in my article. I recommend that you familiarize yourself with it, as well as with a list of sources used.
Since I will be using virtualized domain controllers, I need to change some virtual machine settings, namely disable time synchronization with hypervisor. Time in AD should be synchronized exclusively from external sources. The enabled time synchronization settings with the hypervisor can result in cyclic synchronization and, as a result, problems with the operation of the entire domain.

Note: disabling synchronization with the virtualization host is the easiest and fastest option. However, this is not best practic. According to Microsoft recommendations, you should only partially disable synchronization with the host. To understand the principle of work, read the official documentation, which in recent years has radically jumped up in terms of presentation of the material. .
In general, the approach to administering virtualized domain controllers differs due to some features of AD DS functioning:
Virtual environments present a particular challenge for distributed workflows that rely on time-based replication logic. For example, AD DS replication uses a uniformly incrementing value (called the USN, or Update Sequence Number) assigned to transactions in each domain controller. Each domain controller database instance also receives an identifier called InvocationID. The domain controller's invocationID and its update sequence number together serve as a unique identifier that is associated with each write transaction that occurs on each domain controller and must be unique within a forest.
This completes the basic steps to prepare the environment, proceed to the installation stage.
Installing Active Directory
Installation is done through Server Manager and there is nothing complicated in it, you can see all the installation steps in detail below:


The installation process itself has undergone some changes compared to previous versions of the OS:
Deploying Active Directory Domain Services (AD DS) in Windows Server 2012 is easier and faster than previous versions of Windows Server. AD DS installation is now based on Windows PowerShell and integrated with Server Manager. The number of steps required to introduce domain controllers into an existing Active Directory environment has been reduced.
You only need to select a role Active Directory Domain Services, no additional components need to be installed. The installation process takes a little time and you can immediately proceed to the setup.
When the role is installed, you will see an exclamation mark at the top right of Server Manager - post-deployment configuration is required. Click Promote this server to a domain controller.

Promoting a Server to a Domain Controller
The steps of the wizard are described in detail in the documentation. However, let's go through the basic steps.
Since we are deploying AD from scratch, we need to add a new forest. Be sure to store your Directory Services Restore Mode (DSRM) password securely. The location of the AD DS database can be left at the default (which is what is recommended. However, for variety in my test environment, I specified a different directory).

We are waiting for the installation.

The server will then reboot itself.
Create domain/enterprise administrator accounts
You will need to log in under the local administrator account, as before. Go to snap Active Directory Users and Computers, create the necessary accounts - at this point, this is the domain administrator.

Setting up DNS on a single DC in a domain
During the installation of AD, the AD DNS role was also installed, since I did not have other DNS servers in the infrastructure. For the service to work correctly, you need to change some settings. First you need to check your preferred DNS servers in the network adapter settings. You need to use only one DNS server with the address 127.0.0.1. Yes, it's localhost. By default, it should register itself.

After making sure that the settings are correct, open the DNS snap-in. Right-click on the server name and open its properties, go to the "Forwarder" tab. The DNS server address that was specified in the network settings before installing the AD DS role was automatically registered as the only forwarder:

It is necessary to delete it and create a new one, and it is highly desirable that it be the provider's server, but not a public address such as the well-known 8.8.8.8 and 8.8.4.4. For fault tolerance, register at least two servers. Do not uncheck the box to use root hints if there are no forwarders available. Root hints are a well-known pool of top-level DNS servers.
Adding a second DC to the domain
Since I originally talked about having two domain controllers, it's time to start setting up the second one. We also go through the installation wizard, promote the role to a domain controller, just select Add a domain controller to an existing domain:

Please note that in the network settings of this server, the main The first domain controller configured earlier must be selected as the DNS server! This is required, otherwise you will get an error.
After the necessary settings, log in to the server under the domain administrator account that was created earlier.
Setting up DNS on multiple DCs in a domain
To prevent problems with replication, you need to change the network settings again and you need to do this on each domain controller (and on the pre-existing ones too) and every time you add a new DC:

If you have more than three DCs in the domain, you need to register DNS servers through advanced settings in that order. You can read more about DNS in my article.
Time setting
This step is a must, especially if you're setting up a real environment in production. As you remember, earlier I disabled time synchronization through the hypervisor and now you need to configure it properly. The controller with the FSMO PDC emulator role is responsible for distributing the correct time to the entire domain (Do not know what this role is? Read the article). In my case, this is of course the first domain controller, which is the carrier of all FSMO roles from the very beginning. 
We will configure the time on domain controllers using group policies. As a reminder, domain controller computer accounts are in a separate container and have a separate default group policy. You do not need to make changes to this policy, it is better to create a new one.

Name it as you see fit and how the object will be created, right-click - Change. Go to Computer Configuration\Policies\Administrative Templates\System\Windows Time Service\Time Providers. Activate policies Enable Windows NTP Client and Enable Windows NTP Server, go to the policy properties Configure Windows NTP Client and set the protocol type - NTP, do not touch the rest of the settings:

We are waiting for the policies to be applied (it took me about 5-8 minutes, despite running gpupdate / force and a couple of reboots), after which we get:

In general, it is necessary to make sure that only the PDC emulator synchronizes time from external sources, and not all domain controllers in a row, but this will be the case, since group policy is applied to all objects in the container. You need to redirect it to a specific object of the account of the computer that owns the PDC emulator role. This is also done through group policies - in the gpmc.msc console, left-click the desired policy and on the right you will see its settings. In the security filters, you need to add the account of the desired domain controller:

Read more about the principle of operation and setting up the time service in the official documentation.
This completes the time setting, and with it the initial configuration of Active Directory, is completed.
Active Directory
Active Directory(“Active Directories”, AD) - LDAP-compatible implementation of a corporation's directory service Microsoft for operating systems of the family Windows NT. Active Directory allows administrators to use group policies to ensure a consistent user experience setting, deploy software to multiple computers through group policies or through System Center Configuration Manager(previously Microsoft Systems Management Server), install operating system, application and server software updates on all computers in the network using the Update Service Windows Server . Active Directory stores environment data and settings in a centralized database. networks Active Directory can be of various sizes: from several tens to several million objects.
Performance Active Directory took place in 1999, the product was first released with Windows 2000 Server, and then was modified and improved upon release Windows Server 2003. Subsequently Active Directory has been improved in Windows Server 2003 R2, Windows Server 2008 and Windows Server 2008 R2 and renamed to Active Directory Domain Services. The directory service was formerly called NT Directory Service (NTDS), this name can still be found in some executable files.
Unlike the versions Windows before Windows 2000 who used mainly the protocol NetBIOS for networking, service Active Directory integrated with DNS and TCP/IP. The default authentication protocol is Kerberos. If the client or application does not support authentication Kerberos, the protocol is used NTLM .
Device
Objects
Active Directory has a hierarchical structure consisting of objects. Objects fall into three main categories: resources (such as printers), services (such as email), and user and computer accounts. Active Directory provides information about objects, allows you to organize objects, control access to them, and establishes security rules.
Objects can be containers for other objects (security and distribution groups). An object is uniquely identified by its name and has a set of attributes - characteristics and data that it can contain; the latter, in turn, depend on the type of object. Attributes are the constituent base of an object's structure and are defined in the schema. The schema defines what types of objects can exist.
The schema itself consists of two types of objects: schema class objects and schema attribute objects. One schema class object defines one object type Active Directory(for example, a User object), and one schema attribute object defines an attribute that an object can have.
Each attribute object can be used in several different schema class objects. These objects are called schema objects (or metadata) and allow you to modify and add to the schema as needed. However, each schema object is part of the object definitions Active Directory, so disabling or changing these objects can have serious consequences, since as a result of these actions the structure will be changed Active Directory. The change to the schema object is automatically propagated to Active Directory. Once created, a schema object cannot be deleted, it can only be disabled. Usually, all schema changes are carefully planned.
Container similar object in the sense that it also has attributes and belongs to the namespace , but unlike an object, a container does not stand for anything specific: it can contain a group of objects or other containers.
Structure
The top level of the structure is the forest - the collection of all objects, attributes and rules (attribute syntax) in Active Directory. The forest contains one or more trees connected by transitive relationships of trust . The tree contains one or more domains, also connected in a hierarchy by transitive trust relationships. Domains are identified by their DNS name structures - namespaces.
Objects in a domain can be grouped into containers - OUs. Organizational units allow you to create a hierarchy within a domain, simplify its administration, and allow you to model the organizational and/or geographical structure of a company in Active Directory. Divisions can contain other divisions. Corporation Microsoft recommends using as few domains as possible in Active Directory, and use divisions for structuring and policies. Group policies are often applied specifically to organizational units. Group policies are themselves objects. A division is the lowest level at which administrative authority can be delegated.
Another way to divide Active Directory are sites , which are a way of physical (rather than logical) grouping based on network segments. Sites are divided into those with connections via low-speed channels (for example, via global networks, using virtual private networks) and via high-speed channels (for example, via a local area network). A site may contain one or more domains, and a domain may contain one or more sites. When designing Active Directory it is important to consider the network traffic generated when data is synchronized between sites.
Key design decision Active Directory is the decision to divide the information infrastructure into hierarchical domains and top-level divisions. Typical models used for this separation are the division models by functional divisions of the company, by geographical location and by roles in the company's information infrastructure. Combinations of these models are often used.
Physical structure and replication
Physically, information is stored on one or more equivalent domain controllers that have replaced those used in Windows NT primary and backup domain controllers, although a so-called "single-master operations" server, which can emulate a primary domain controller, is retained for some operations. Each domain controller keeps a read/write copy of the data. Changes made on one controller are synchronized to all domain controllers during replication. Servers where the service itself Active Directory not installed, but which are included in the domain Active Directory, are called member servers.
replication Active Directory performed upon request. Service Knowledge Consistency Checker creates a replication topology that uses the sites defined in the system to manage traffic. Intrasite replication is performed frequently and automatically by a consistency checker (by notifying replication partners of changes). Replication between sites can be configured for each channel of a site (depending on the quality of the channel) - a different "rate" (or "cost") can be assigned to each channel (for example DS3, , ISDN etc.) and replication traffic will be limited, scheduled, and routed according to the assigned link estimate. Replication data can transitively travel across multiple sites via site link bridges if the "score" is low, although AD automatically assigns a lower score for site-to-site links than for transitive links. Site-to-site replication is performed by bridgehead servers in each site, which then replicate the changes to each domain controller in their site. Intradomain replication takes place according to the protocol RPC protocol IP, cross-domain - can also use the protocol SMTP.
If the structure Active Directory contains several domains, to solve the problem of finding objects, it is used global catalog: A domain controller that contains all the objects in the forest, but with a limited set of attributes (a partial replica). The catalog is stored on specified global catalog servers and serves cross-domain requests.
The single host capability allows requests to be handled when multi-host replication is not allowed. There are five types of such operations: Domain Controller Emulation (PDC Emulator), Relative Identifier Host (Relative Identifier Master or RID Master), Infrastructure Host (Infrastructure Master), Schema Host (Schema Master), and Domain Naming Host (domain naming master). The first three roles are unique within the domain, the last two are unique within the entire forest.
base Active Directory can be divided into three logical stores or "partitions". The schema is a template for Active Directory and defines all object types, their classes and attributes, attribute syntax (all trees are in the same forest because they have the same schema). The configuration is the structure of the forest and trees Active Directory. A domain stores all information about objects created in that domain. The first two stores are replicated to all domain controllers in the forest, the third partition is fully replicated between replica controllers within each domain and partially replicated to global catalog servers.
naming
Active Directory supports the following object naming formats: generic type names UNC, URL and LDAP URL. Version LDAP X.500 naming format is used internally Active Directory.
Each object has distinguished name (English) distinguished name, DN) . For example, a printer object named HPLaser3 in the Marketing OU and in the domain foo.org will have the following DN: CN=HPLaser3,OU=Marketing,DC=foo,DC=org , where CN is the common name, OU is the section, and DC is the domain object class. Distinguished names can have many more parts than the four parts in this example. Objects also have canonical names. These are the distinguished names written in reverse order, without identifiers and using forward slashes as separators: foo.org/Marketing/HPLaser3 . To define an object within its container, use relative distinguished name : CN=HPLaser3 . Each object also has a globally unique identifier ( GUID) is a unique and immutable 128-bit string that is used in Active Directory for search and replication. Certain objects also have a user principal name ( UPN, in accordance with RFC 822) in the format object@domain.
Integration with UNIX
Various levels of interaction with Active Directory can be implemented in most UNIX-like operating systems through standard-compliant LDAP clients, but such systems typically do not understand most of the attributes associated with components Windows such as group policies and support for one-way trusts.
Third party vendors offer integration Active Directory on platforms UNIX, including UNIX, linux, MacOS X and a number of applications based Java, with product package:
Schematic add-ons supplied with Windows Server 2003 R2 include attributes that are closely enough related to RFC 2307 to be of general use. RFC 2307 base implementations, nss_ldap and pam_ldap , proposed PADL.com, directly support these attributes. The standard scheme for group membership follows RFC 2307bis (proposed). Windows Server 2003 R2 includes the Microsoft Management Console for creating and editing attributes.
An alternative is to use another directory service like 389 Directory Server(previously Fedora Directory Server, FDS), eB2Bcom ViewDS v7.1 XML Enabled Directory or Sun Java System Directory Server from Sun Microsystems, which performs two-way synchronization with Active Directory, thus implementing "reflected" integration when clients UNIX and linux are authenticated FDS, and clients Windows are authenticated Active Directory. Another option is to use OpenLDAP with the possibility of translucent overlay, expanding the elements of the remote server LDAP additional attributes stored in the local database.
Active Directory automated using Powershell .
Literature
- Rand Morimoto, Kenton Gardiner, Michael Noel, Joe Koka Microsoft Exchange Server 2003. Complete Guide = Microsoft Exchange Server 2003 Unleashed. - M .: "Williams", 2006. - S. 1024. - ISBN 0-672-32581-0
see also
Links
Notes
| Microsoft Windows Components | |
|---|---|
| Main | |
| Services management |
|
| Applications |
Contact DVD Maker Fax and Scan Internet Explorer Magazine Magnifier media center Windows Media Player Collaboration Program Windows Mobile Device Center Mobility Center Narrator Paint Personal character editor Remote Assistance Speech recognition word pad Notebook Side panel sound recording Calendar Calculator Scissors Mail symbol table historical: Movie Maker NetMeeting Outlook Express Program Manager File Manager Photo album |
| Games | |
| OS kernel | |
| Services | |
| File systems |
|
| Server |
Active Directory Deployment Services File Replication Service DNS Domains Folder redirection Hyper-V IIS Media Services MSMQ Network Access Protection (NAP) Print Services for UNIX Remote Differential Compression Remote Installation Services Rights Management Service Roaming user profiles SharePoint System Resource Manager Remote Desktop WSUS Group Policy Distributed transaction coordinator |
| Architecture | |
| Security | |
| Compatibility | |
| Microsoft | ||
|---|---|---|
| ON | ||
| Server software | ||
| Technology | ||
| Internet | ||
| Games | ||
| Hardware security |
||
| Education | ||
| Licensing | ||
| Subdivisions | ||
Active Directory is a system management service. They are a much better alternative to local groups and allow you to create computer networks with efficient management and reliable data protection.
If you have not come across the concept of Active Directory before and do not know how such services work, this article is for you. Let's see what this concept means, what are the advantages of such databases and how to create and configure them for initial use.
Active Directory is a very convenient way to manage systems. With Active Directory, you can effectively manage your data.
These services allow you to create a single database managed by domain controllers. If you own a business, manage an office, or generally control the activities of many people who need to be brought together, you will need such a domain.
It includes all objects - computers, printers, fax machines, user accounts, and so on. The sum of the domains where the data resides is referred to as a "forest". An Active Directory base is a domain environment where the number of objects can be up to 2 billion. Can you imagine these scales?
That is, with the help of such a “forest” or database, you can connect a large number of employees and equipment in the office, and without being tied to a place - other users can also be connected in services, for example, from a company office in another city.
In addition, within the framework of Active Directory services, several domains are created and combined - the larger the company, the more funds are needed to control its technology within the database.
Further, when creating such a network, one controlling domain is determined, and even with the subsequent presence of other domains, the original one still remains the “parent” - that is, only it has full access to information management.
Where is this data stored, and what ensures the existence of domains? Controllers are used to create an Active Directory. Usually there are two of them - if something happens to one, the information will be stored on the second controller.

Another option for using the base is if, for example, your company cooperates with another, and you have to complete a common project. In this case, it may be necessary for unauthorized persons to access the files of the domain, and here you can set up a kind of “relationship” between two different “forests”, open access to the required information without risking the security of other data.
In general, Active Directory is a means for creating a database within a certain structure, regardless of its size. Users and all equipment are combined into one "forest", domains are created and placed on controllers.
It is also advisable to clarify - the operation of services is possible only on devices with Windows server systems. In addition, 3-4 DNS servers are created on the controllers. They serve the main zone of the domain, and in the event that one of them fails, it is replaced by other servers.
After a brief overview of Active Directory for dummies, you are naturally wondering - why change the local group to the whole database? Naturally, the field of possibilities is much wider here, and in order to find out other differences between these services for system management, let's take a closer look at their advantages.
Benefits of Active Directory
The advantages of Active Directory are as follows:
- Using a single resource for authentication. In this scenario, you need to add on each PC all accountsrequiring access to general information. The more users and equipment, the more difficult it is to synchronize this data between them.
And so, when using services with a database, accounts are stored at one point, and changes take effect immediately on all computers.
How it works? Each employee, coming to the office, launches the system and logs into his account. The login request will be automatically submitted to the server, and authentication will occur through it.
As for a certain order in keeping records, you can always divide users into groups - "HR" or "Accounting".
It is even easier in this case to provide access to information - if you need to open a folder for employees from one department, you do it through the database. Together they get access to the required data folder, while for the rest the documents remain closed.
- Control over each member of the database.
If in a local group each member is independent, it is difficult to control it from another computer, then certain rules can be set in domains that correspond to company policy.
As a system administrator, you can set access and security settings, and then apply them for each user group. Naturally, depending on the hierarchy, some groups can be defined more stringent settings, while others can be granted access to other files and actions in the system.
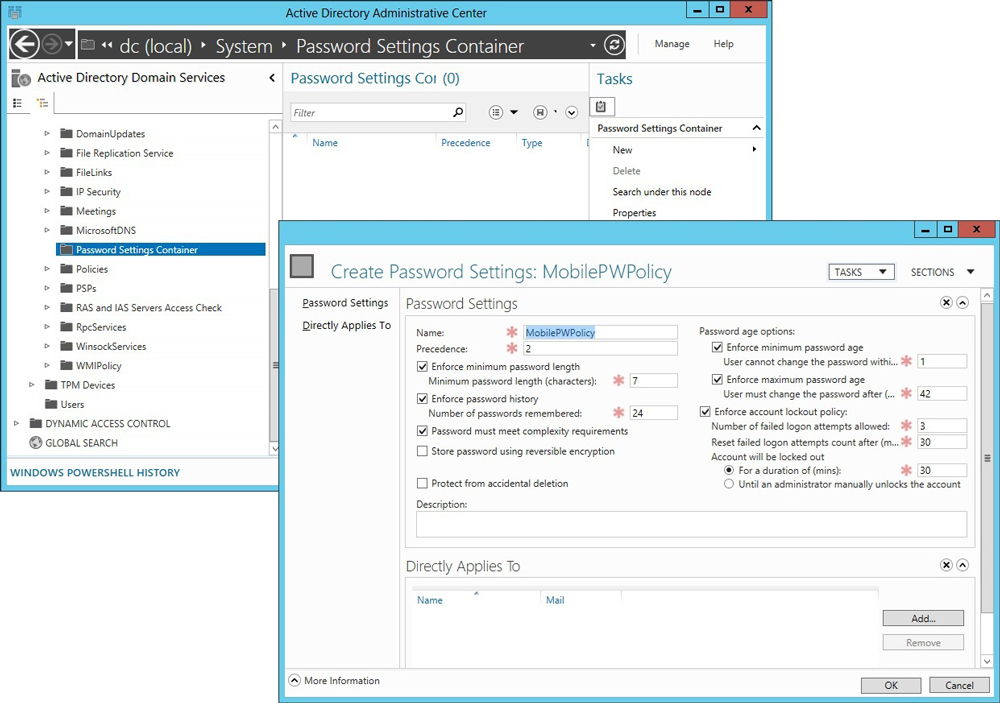
In addition, when a new person enters the company, his computer will immediately receive the necessary set of settings, where the components for work are included.
- Versatility in software installation.
By the way, about the components - with the help of Active Directory, you can assign printers, install the necessary programs immediately for all employees, and set privacy settings. In general, the creation of a database will significantly optimize the work, monitor security and unite users for maximum efficiency.
And if the company operates a separate utility or special services, they can be synchronized with domains and make it easier to access them. How? If you combine all the products used in the company, the employee will not need to enter different logins and passwords to enter each program - this information will be common.
Now that the benefits and meaning of using Active Directory are clear, let's look at the process of installing these services.
Using a database on Windows Server 2012
Installing and configuring Active Directory is not difficult, and it is also easier than it seems at first glance.
To load services, first you need to do the following:
- Change the name of the computer: click on "Start", open the Control Panel, item "System". Select "Change settings" and in Properties opposite the "Computer name" line, click "Change", enter a new value for the host PC.
- Reboot as required by the PC.
- Set the network settings like this:
- Through the control panel, open the menu with networks and sharing.
- Correct adapter settings. Right-click "Properties" and open the "Network" tab.
- In the window from the list, click on the Internet Protocol at number 4, click on "Properties" again.
- Enter the required settings, for example: IP address - 192.168.10.252 , subnet mask - 255.255.255.0, main sub-gateway - 192.168.10.1.
- In the line "Preferred DNS server" specify the address of the local server, in "Alternative ..." - other addresses of DNS servers.
- Save changes and close windows.
Install the Active Directory roles like so:
- Through the start, open "Server Manager".
- From the menu, select Add roles and features.
- The wizard will start, but you can skip the first description window.
- Check the line "Install roles and features", move on.
- Select your computer to put Active Directory on it.
- From the list, check the role you want to load - for your case, this is "Active Directory Domain Services".
- A small window will appear asking you to download the components required for the services - accept it.
- After you will be prompted to install other components - if you do not need them, just skip this step by clicking "Next".
- The setup wizard will display a window with descriptions of the services you are installing - read on and move on.
- A list of components that we are going to install will appear - check if everything is correct, and if so, click on the appropriate button.
- Close the window when the process is complete.
- That's it - the services are loaded on your computer.

Configuring Active Directory
To set up a domain service, you need to do the following:
- Launch the setup wizard of the same name.
- Click on the yellow pointer at the top of the window and select "Promote the server to a domain controller".
- Click on add a new "forest" and create a name for the root domain, then click "Next".
- Specify the operating modes of the "forest" and the domain - most often they coincide.
- Create a password, but be sure to remember it. Move on.
- After that, you may see a warning that the domain is not delegated and a suggestion to check the domain name - you can skip these steps.
- In the next window, you can change the path to the database directories - do this if they do not suit you.
- Now you will see all the options that you are going to set - see if you have chosen them correctly and move on.
- The application will check if the prerequisites are met, and if there are no comments, or they are not critical, click "Install".
- After the installation is complete, the PC will reboot itself.
You may also be wondering how to add a user to the database. To do this, use the "Active Directory Users or Computers" menu, which you will find in the "Administration" section in the control panel, or use the database settings menu.
To add a new user, right-click on the domain name, select "Create", after "Subdivision". A window will appear in front of you where you need to enter the name of the new department - it serves as a folder where you can collect users from different departments. In the same way, you will later create several more divisions and correctly place all the employees.
Next, when you have created the name of the department, right-click on it and select "Create", after - "User". Now it remains only to enter the necessary data and set the access settings for the user.
When a new profile is created, click on it by selecting the context menu and open "Properties". In the "Account" tab, uncheck the box next to "Block ...". That's all.
The general conclusion is that Active Directory is a powerful and useful tool for system management, which will help to unite all employees' computers into one team. With the help of services, you can create a secure database and significantly optimize the work and synchronization of information between all users. If your company and any other place of work is connected to electronic computers and the network, you need to consolidate accounts and keep track of work and privacy, installing an Active Directory-based database will be a great solution.
Being well acquainted with small business from the inside, I have always been interested in the following questions. Explain why the employee should use the browser that the system administrator likes on the work computer? Or take any other software, for example, the same archiver, email client, instant messaging client ... This I smoothly hint at standardization, and not on the basis of the personal sympathy of the system administrator, but on the basis of the sufficiency of functionality, cost of maintenance and support of these software products. Let's start to consider IT as an exact science, not a craft, when everyone does what they can. Again, there are a lot of problems with this in small businesses too. Imagine that a company is changing several such administrators in a difficult time of crisis, what should poor users do in such a situation? Relearn constantly?
Let's look from the other side. Any leader should understand what is happening in the company (including in IT) now. This is necessary to monitor the current situation, to quickly respond to the emergence of various kinds of problems. But this understanding is more important for strategic planning. Indeed, having a strong and reliable foundation, we can build a house on 3 or 5 floors, make a roof of various shapes, make balconies or a winter garden. Similarly, in IT, we have a solid foundation - we can continue to use more complex products and technologies to solve business problems.
In the first article, we will talk about such a foundation - Active Directory services. They are designed to become a strong foundation for the IT infrastructure of a company of any size and any line of business. What it is? Let's talk about it here...
And let's start the conversation with simple concepts - domain and Active Directory services.
Domain is the main administrative unit in the network infrastructure of an enterprise, which includes all network objects, such as users, computers, printers, shares, and more. The collection of such domains is called a forest.
Active Directory Services (Active Directory Services) is a distributed database that contains all domain objects. The Active Directory domain environment is a single point of authentication and authorization for users and applications across the enterprise. It is with the organization of the domain and the deployment of Active Directory services that the construction of the IT infrastructure of the enterprise begins.
The Active Directory database is stored on dedicated servers - domain controllers. Active Directory Services is a role of Microsoft Windows Server operating systems. Active Directory Services is highly scalable. More than 2 billion objects can be created in an Active Directory forest, making it possible to implement a directory service in companies with hundreds of thousands of computers and users. The hierarchical structure of domains allows you to flexibly scale your IT infrastructure to all branches and regional divisions of companies. For each branch or division of the company, a separate domain can be created, with its own policies, its own users and groups. For each child domain, administrative authority can be delegated to local system administrators. At the same time, child domains are still subordinate to the parent ones.
In addition, Active Directory services allow you to set up trust relationships between domain forests. Each company has its own forest of domains, each with its own resources. But sometimes it may be necessary to provide access to your corporate resources to employees of another company - work with shared documents and applications as part of a joint project. To do this, trust relationships can be set up between the forests of organizations, which will allow employees of one organization to log in to the domain of another.
To provide fault tolerance for Active Directory services, you must deploy two or more domain controllers in each domain. All changes are automatically replicated between domain controllers. In the event of a failure of one of the domain controllers, the network is not affected, because the remaining ones continue to work. An additional layer of resiliency is provided by hosting DNS servers on domain controllers in Active Directory, which allows each domain to have multiple DNS servers serving the primary domain zone. And if one of the DNS servers fails, the rest will continue to work. We will talk about the role and importance of DNS servers in the IT infrastructure in one of the articles in the series.
But these are all technical aspects of implementing and maintaining Active Directory services. Let's talk about the benefits a company gets by moving away from peer-to-peer networking using workgroups.
1. Single point of authentication
In a workgroup on each computer or server, you will have to manually add a complete list of users who need network access. If suddenly one of the employees wants to change his password, then it will need to be changed on all computers and servers. Well, if the network consists of 10 computers, but if there are more? When using an Active Directory domain, all user accounts are stored in one database, and all computers access it for authorization. All domain users are included in the appropriate groups, for example, "Accounting", "Financial Department". It is enough to set permissions for certain groups once, and all users will receive the appropriate access to documents and applications. If a new employee comes to the company, an account is created for him, which is included in the appropriate group - the employee gets access to all network resources to which he should be allowed access. If an employee quits, it is enough to block - and he will immediately lose access to all resources (computers, documents, applications).
2. Single point of policy management
In a workgroup, all computers are equal. None of the computers can control the other, it is impossible to control compliance with uniform policies and security rules. When using a single Active Directory directory, all users and computers are hierarchically distributed into organizational units, each of which is subject to uniform group policies. Policies allow you to set uniform settings and security settings for a group of computers and users. When a new computer or user is added to the domain, it automatically receives settings that comply with accepted corporate standards. With the help of policies, you can centrally assign network printers to users, install the necessary applications, set browser security settings, and configure Microsoft Office applications.
3. Increased level of information security
Using Active Directory services greatly improves network security. Firstly, it is a single and secure storage of accounts. In a domain environment, all passwords for domain users are stored on dedicated servers - domain controllers, which are usually protected from external access. Secondly, when using a domain environment, the Kerberos protocol is used for authentication, which is much more secure than the NTLM used in workgroups.
4. Integration with corporate applications and equipment
A big advantage of Active Directory services is compliance with the LDAP standard, which is supported by other systems, such as mail servers (Exchange Server), proxy servers (ISA Server, TMG). And it is not necessarily only Microsoft products. The advantage of this integration is that the user does not need to remember a large number of logins and passwords to access a particular application, in all applications the user has the same credentials - his authentication takes place in a single Active Directory. Windows Server provides Active Directory integration with the RADIUS protocol, which is supported by a wide variety of network equipment. Thus, it is possible, for example, to provide authentication of domain users when connecting via VPN from the outside, the use of Wi-Fi access points in the company.
5. Unified Application Configuration Store
Some applications store their configuration in Active Directory, such as Exchange Server. Deploying the Active Directory directory service is a prerequisite for these applications to work. Storing application configuration in a directory service is beneficial in terms of flexibility and reliability. For example, in the event of a complete failure of the Exchange server, its entire configuration will remain intact. To restore the functionality of corporate mail, it will be enough to reinstall Exchange Server in recovery mode.
Summing up, I would like to once again focus on the fact that Active Directory services are the heart of an enterprise's IT infrastructure. In the event of a failure, the entire network, all servers, the work of all users will be paralyzed. No one will be able to log into the computer, access their documents and applications. Therefore, the directory service must be carefully designed and deployed, taking into account all possible nuances, for example, the bandwidth of channels between branches or company offices (this directly affects the speed of user login to the system, as well as data exchange between domain controllers).














